De.Fi Scanner Review
De.Fi Scanner
de.fi
De.Fi Scanner Review: Fast Token Risk Checks (Honeypot, Mint, Blacklist) + FAQ
About to ape into a new token and want a fast, honest risk check before you hit “swap”?
You’re in the right place. In this review, I’m going to show you exactly how to use De.Fi Scanner to spot red flags in seconds, avoid traps like honeypots and hidden mints, and build a safer workflow before you click confirm. The goal is simple: less guessing, clearer signals, and a checklist you can reuse across chains.
Describe problems or pain
Scams and risky contracts are sneaky. They hide in plain sight with “features” that flip the game on you after you buy. Here are the ones I see most:
- Honeypots and transfer blocks — you can buy but can’t sell, or transfers fail under certain conditions.
- Stealth minting and supply tricks — a backdoor that lets someone mint infinite tokens after launch.
- Blacklist and pause functions — holder-specific blocks or a “kill switch” to halt trading when it hurts you most.
- Tax traps — low fee at launch, then a sudden 20–100% sell tax after hype builds.
- Proxy upgrades — code can be swapped out post-launch without you knowing, changing the rules mid-game.
- Unlimited approvals — one sloppy click and a malicious contract can move your tokens later.
This isn’t theoretical. Research published by Solidus Labs found over 117,000 scam tokens in one year, and Chainalysis’ crime reports continue to show billions siphoned via scams and contract exploits over time. Phishing and wallet-drainer kits alone cost users hundreds of millions annually (see ScamSniffer’s reports). Most people only learn the warning signs after losing funds.
On top of that, there’s tool overload. Which scanner do you trust? Which signals matter? What do you actually do when a warning pops up?
Promise solution
Here’s the plan: I’ll show you what De.Fi Scanner checks, how accurate it is in practice, and how to use it in under a minute. Then we’ll fold it into a repeatable checklist you can apply to any token. You’ll see how to pair the scan with approval revokes and a couple of quick sanity checks so you act, not react.
How I test tools
I pressure-test scanners with real tokens and known-bad contracts, then compare the flags to manual checks on explorers and docs. I mark down false positives, note what a tool misses, and verify whether the warnings are actionable. A few recent examples from my notes:
- Upgradeable + owner-only: Scanner flagged a proxy-controlled token with owner-settable fees. Later, fees spiked post-launch. Easy pass.
- Blacklist pattern: Scan highlighted blacklist/anti-bot hooks. Early buyers ended up unable to sell on specific routes. Warning matched the outcome.
- Mint risk: Contract looked clean on socials, but scan caught mint permissions tucked behind a role. A stealth supply jump followed. Saved me a headache.
- Honeypot edge case: One hyper-optimized token used exotic transfer logic; initial tool output was inconclusive. A tiny test trade + manual read confirmed it was sell-blocked under load. Treat scanners as a first pass, not gospel.
What you’ll learn
- What De.Fi Scanner is and how it works across chains
- The exact risks it flags: honeypot, mint, blacklist, upgradeability, fees, ownership
- How to read the score and what actions to take
- Limits, pricing, and privacy basics
- How it stacks against TokenSniffer, GoPlus, and others
- Quick answers to the questions everyone asks
TL;DR snapshot
De.Fi Scanner is a fast, multi-chain contract scanner with clear red/amber/green checks and built-in approval revoke links. It’s great for pre-trade filtering and catching obvious traps quickly. It’s not a replacement for audits or manual code review—use it as your first pass, not your final verdict.
Ready to see how it actually works and why it deserves a spot on your first screen? Let’s look at what it checks and how to read the results in under a minute.
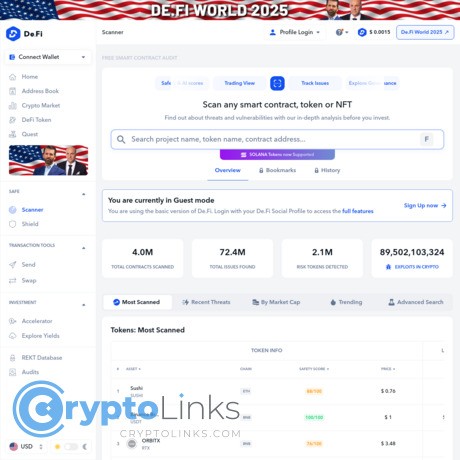
What is De.Fi Scanner and why I keep it on my first screen
De.Fi Scanner is a web-based contract scanner that grades token risk and explains why. I paste a contract, hit scan, and in seconds I get a color-coded risk score with the exact checks that passed, warned, or failed—honeypots, taxes, blacklist functions, mint/ownership powers, upgradeability, and more. It’s built by the De.Fi team (the same folks behind their antivirus and approval revoke tools), and it has one job: stop obvious traps before they stop you.
I keep it open because speed matters. Last week, a hyped Base token looked fine on socials but Scanner flagged owner-controlled fees and an upgradeable proxy. That was enough to size down and wait. Another time on BNB Chain, a memecoin returned a sell-blocking honeypot warning—saved me a “buy, can’t sell” headache and a pile of gas fees.
“In crypto, the difference between a win and a wipeout is often 60 seconds of checking.”
That 60 seconds isn’t optional anymore. Independent reports (see Chainalysis crime research and De.Fi’s own REKT Database) keep showing billions in annual losses across scams, exploits, and permissions abuse. A fast scanner won’t catch everything, but it narrows the field so you don’t gamble blind.
Core features at a glance
- Clear risk score with pass / warn / fail checks you can read in seconds.
- Honeypot, tax, and transfer tests on popular chains to spot “buy only” traps or predatory fees.
- Ownership and permissions analysis: mint, pause, blacklist, fee changes, and who controls upgrades.
- Proxy/upgradeable detection with controller addresses so you know if logic can be swapped tomorrow.
- Approval safety tie-in: quick links to revoke risky allowances via De.Fi’s revoke tools.
- Readable, actionable report: plain-English flags and short explanations so you know what to do next.
Example outcomes I often see:
- “Potential honeypot detected”: buying may work, selling fails or costs 99%—instant pass from me.
- “Owner can mint unlimited supply”: possible stealth dumps; I treat this as high risk unless the team is public and audited.
- “Upgradeable proxy controlled by X”: code can change; I’ll check the controller’s reputation and history before risking capital.
- “Blacklist enabled”: the contract can block wallets; not always malicious, but a big trust decision.
Why it matters right now
New tokens are launching around the clock, especially during memecoin bursts and narrative rotations. Scammers recycle the same tricks with fresh wrappers—just enough to slip past casual checks. A fast scanner gives you a gut-check on:
- Can I actually sell? (honeypot and transfer checks)
- Can the team nuke me later? (mint, blacklist, pause, fee control)
- Can the code change post-hype? (proxy/upgradeability)
When you see a wall of green, you still verify the basics. When you see a red or two, you know where to dig—or when to walk. It’s the difference between chasing every shiny thing and playing the odds with a plan.
“Trust, but verify—then verify again before you hit ‘swap.’”
Supported environments
Scanner runs in your browser—no install, no extensions. Paste a contract and select the chain. It supports major EVM networks like Ethereum, BNB Chain, Polygon, Arbitrum, Base, Optimism, and Avalanche (coverage and specific checks can vary by chain). Some checks—like LP lock status or holder concentration—may require an extra look on a block explorer depending on the network and token type.
If you’re testing non-standard tokens or newer chains, expect the occasional “limited data” message—better that than a false green. I’ll take honest gaps over confident guesses any day.
So what exactly does it look for under the hood—honeypots, hidden mints, upgradeability, blacklist powers—and how do you read those red/yellow/green signals without second-guessing yourself? Let’s break that down next.
What Scanner actually checks (and how to read the results)
When I paste a contract into De.Fi Scanner, I’m not looking for magic. I’m looking for fast, clear signals that tell me if the code can fight back when I want to sell, mint behind my back, or change the rules mid-game. Here’s what actually gets checked and how I read it without getting lost in the weeds.
“The contract is the truth; marketing is noise.”
Token mechanics and trading risks
These are the checks that save you from the classic “can’t sell” nightmare and sneaky fee traps:
- Honeypot / transfer blocking: Scanner simulates transfers to see if you can buy but not sell, or if sells fail for non-owners. If it flags a honeypot, I treat that as a hard stop. I’ve seen tokens where buys succeed, but sells revert unless a hidden allowlist is set. If you’ve ever watched a chart go up forever while holders scream in chat… that’s the pattern.
- Buy/Sell tax and sudden fee changes: It surfaces fee variables and who can change them. Fees that can jump from 5% to 100% after launch are a red flag. I’ve caught contracts where the owner can push sell tax to 99%, effectively trapping exit liquidity without blocking sells outright.
- Trading pausability and blacklists: Some tokens include pause or blacklist functions that let the controller freeze trading or target specific wallets. That might be “for bot control,” but it’s still a power you’re trusting them with. If Scanner shows a blacklist function, I assume it can be abused on a bad day.
Quick reality check: Research from teams like Chainalysis and security firms consistently shows that rug-pull tokens often use a mix of transfer restrictions and aggressive fee mechanics. The code tricks don’t need to be fancy; they just need to be timed right.
Ownership and control
This is where good tokens separate themselves from “change the rules later” tokens:
- Is ownership renounced? If ownership is renounced, the key admin levers should be gone. If not, I want to know exactly what the owner can still do.
- Admin powers: mint, pause, fee changes: Scanner flags functions like mint, pause, setFees, setMaxTx, setBlacklist. It also notes if those powers are behind a role (Ownable, AccessControl) and who holds it. Silent mints after launch are one of the fastest ways to nuke a chart.
- Upgradeable/proxy patterns and who controls them: If the contract is a proxy, I check who controls the proxy admin. Upgrades can ship new logic overnight. The OpenZeppelin docs make this clear: upgradeable proxies are powerful and safe when governed well, dangerous when not. If an anonymous team controls upgrades, I assume higher risk.
Example I see often: A token launched as “community-owned,” but Scanner shows a UUPS proxy with an upgrade admin still in a dev wallet. That’s not community-owned; that’s permissioned risk wrapped in a meme.
Supply, liquidity, and distribution hints
These checks aren’t crystal balls, but they point me to the right follow-ups:
- Mintable supply or hidden mints: If the token is mintable and no cap is enforced, inflation risk is real. Scanner flags minter roles and relevant functions so you don’t have to spelunk the code.
- Liquidity lock status (if detectable): It tries to detect burned LP or locked LP via known lockers. If it can’t confirm, I manually verify on the LP token page. Unlocked LP is a classic “pull the plug” risk.
- Top holder concentration: Warnings appear when a few wallets hold a big chunk of supply. I watch for patterns like:
- “Owner + two wallets” holding 60%+
- Multiple fresh wallets funded from the same source (sybil pattern)
- Dead address balances that aren’t actually dead (a fake burn)
One pattern that keeps paying to notice: A token with “burned” supply to a non-zero address that still has transfer rights. Scanner won’t call every trick, but it nudges me to confirm whether that “burn” is irreversible.
How to interpret the score
Scanner rolls these checks into a simple traffic-light score. I don’t treat it as gospel; I treat it as a map:
- Green: It passed the common traps. I still verify basics—LP status, owner context, and whether fees are fixed. Green means “nothing obvious,” not “safe forever.”
- Yellow: There’s a specific risk you need to understand. Maybe fees are adjustable, or it’s upgradeable with a known team. I size small and watch for changes. Yellow is fine for a test buy if the narrative and team check out.
- Red: Honeypot, blacklist control, mint rights, or unlocked LP with no plan. Unless I fully understand the contract and the team has earned trust, I assume high risk and move on.
Your gut might be shouting “this one’s going to the moon.” The score is your cooler head. It doesn’t kill opportunity; it stops avoidable pain. As the old line goes, “trust, but verify.”
Want the exact 60‑second routine I use to turn this report into a go/no‑go decision, including the two extra checks that save me from FOMO-errors? Keep reading—next up I’ll show you the quick workflow that keeps me out of traps without slowing me down.
Step-by-step: my 60‑second Scanner workflow
I keep this fast, ruthless, and repeatable. The whole point is to catch the obvious traps before emotions take over. As I always remind myself: “If you can’t explain the risk in one sentence, you can’t explain the loss to yourself later.”
Step 1: Paste the contract, confirm chain, hit scan
Open de.fi/scanner, paste the contract, select the right chain, and run it.
- Verify you’ve got the real address: copy it from the official site/X/Discord, then cross-check the last 6–8 characters against a block explorer like Etherscan or BscScan. Fake token pages with look‑alike tickers are everywhere.
- Contract must be verified: if the code isn’t verified on the explorer, that’s an instant pause for me. Unverified means you can’t truly see what you’re signing up for.
- Match the chain to the pair you’ll trade: I’ve seen people paste an ETH address, then buy a BSC clone. Easy way to get wrecked. If you found the token via a DEX pair, grab the token address from that pair’s page directly.
Step 2: Skim the top warnings first
I scan the top three signals and decide in seconds if it’s worth more time:
- Honeypot/transfer blocked flagged? I stop. No exceptions. If I’m stubbornly curious, I’ll run a $1 test buy and sell on a low‑fee chain, but 99% of the time this is a pass.
- Mint/blacklist/fee control? If mint or blacklist shows up, I read exactly who can call it. If the owner can set fees or pause trading without a timelock/multisig, risk shoots up. I’ve watched “safe” tokens flip a 2% sell tax to 50% mid‑hype because the owner had that power. Scanner’s owner-permission flags are your early siren.
- Upgradeable/proxy? Upgradeable contracts aren’t evil, but they’re a lever. I click through to the proxy on the explorer (look for “Read as Proxy” on Etherscan) and check the admin. If it’s a single EOA, I size down. If it’s a multisig or a timelock, that’s better. Want a quick refresher on proxy risks? See OpenZeppelin’s proxy docs and EIP‑1967.
Pro tip: Repeated patterns matter. Multiple security write‑ups over the years show owner-controlled fee setters and blacklist functions are common rug vectors. When Scanner highlights them, I assume they’ll be used at the worst possible time.
Step 3: Cross-check liquidity and holders
Scanner’s hints are a start. I confirm the money plumbing before I touch anything:
- LP lock: On the DEX pair page (via Dexscreener), I hunt for a lock link (e.g., Unicrypt, Team Finance, PinkLock). No lock? I assume the LP can be yanked. For Uniswap v3 (no LP tokens), I check who owns the position NFTs and whether there’s any timelock or multisig custody.
- Top holders: On the explorer’s “Holders” tab, I exclude the dead/burn wallet and CEX wallets. As a rule of thumb:
- Deployer/top wallet >10–15% = caution.
- Top 10 wallets >50% (excluding LP/burn) = heavy caution.
- LP held by a normal EOA (not a locker) = I usually pass.
- Recent transfers: I peek at recent internal/external txs. Sudden mints to fresh wallets or a lot of blacklist events = gone.
Real example from my notes: a BSC meme coin looked “green enough,” but Scanner warned “owner can set fees.” Holders showed one wallet with 65% supply and no LP lock. That’s three separate outs the team could pull. I passed, and 24 hours later taxes spiked to 30%. The chart told the rest.
Step 4: Decide action
Now I put it in a box: green, yellow, or red—and act without second‑guessing.
- Green / low risk + sensible tokenomics:
- Small test buy first (tiny, then confirm you can sell).
- Keep slippage tight; high slippage is MEV bait and “hidden tax” friendly.
- Set price and liquidity alerts on Dexscreener or your bot of choice.
- Yellow / known owner controls or partial gaps:
- Reduce size and timebox the trade. I plan exits before entries.
- Watch for promises: “renounce soon” or “LP lock incoming.” If they actually do it, I reconsider.
- Re‑scan after any contract or ownership change.
- Red / honeypot, mint on, blacklist, unlocked LP:
- I pass. If curiosity wins, it’s play money only—and I still test a sell immediately.
- Screenshot the warnings. It helps curb FOMO when your feed turns loud.
“Trust is a luxury. Verification is a habit.”
One last thing: even a “green” scan won’t save you if you hand out unlimited approvals like candy. Want the quick method I use to tighten approvals and clean my wallet after testing new DApps? That’s exactly what I’m showing next—how I use revoke tools to shut the doors scammers love to pry open. Ready to lock those down?
Going beyond the scan: approvals, revokes, and portfolio hygiene
The fastest way to get wrecked isn’t always a bad trade—it’s a quiet, unlimited approval you forgot about months ago. Scans catch contract risks, but approvals are what let those contracts move your assets. That’s where I go on offense.
"It’s not the red candle that drains you. It’s the invisible permission you signed last summer."
Why approvals matter
When you “approve” a token, you’re letting a contract spend your tokens via allowance. Most DEXs ask for unlimited approvals so you don’t have to reapprove every trade. That’s convenient, but if that contract (or a spoofed lookalike you connected to) turns malicious, it can pull everything you approved—without asking again.
- ERC‑20 allowance (approve/transferFrom): lets a spender move your tokens until you set it back to 0.
- Permit / EIP‑2612: a gasless signature that creates an allowance—drainers love this because you think you “just signed a message.”
- Permit2: a Uniswap standard for spending; safe when used right, abused by phishers when you sign blind.
- ERC‑721/1155 setApprovalForAll: one click can let a marketplace—or a fake one—move all your NFTs.
This isn’t hypothetical. ScamSniffer’s 2023 report tracked roughly $295M lost to phishing, with most thefts relying on malicious approvals, Permit/Permit2 signatures, and setApprovalForAll. Think fake airdrops, bogus support chats, sponsored search ads—one signature and you’re done.
Use De.Fi’s revoke/antivirus tools
Scanning a token is step one. Step two is clearing permissions you don’t need. Here’s how I keep it tight with De.Fi’s revoke and antivirus:
- Go to De.Fi and open their Revoke/Antivirus section.
- Connect the wallet you use for trading. Sort approvals by token and spender.
- Revoke anything you don’t recognize or no longer use. Yes, it costs a bit of gas—cheap on L2s, worth it on mainnet for stables/NFTs.
- Use the antivirus-style overview to spot risky approvals across chains and apps in one place.
What I revoke first:
- Unlimited approvals for stablecoins (USDT/USDC/DAI) to old routers or random dApps.
- setApprovalForAll on NFTs to anything except your active marketplace—and even then, I timebox it.
- Permit/Permit2 allowances I don’t remember signing, or tied to airdrop claimers.
- LP/router approvals that are older than 60–90 days (projects and endpoints change).
Pro tip: some tokens (like USDT) use a “set to 0 then set new allowance” pattern. Revoking with De.Fi handles the reset flow—so don’t be surprised if it takes two transactions in rare cases.
Simple safety habits
Approvals hygiene is a habit, not a one-off chore. Here’s the short list I actually stick to:
- Use fresh wallets for new mints and unproven dApps. If it goes bad, your core stack is untouched.
- Separate savings and trading: cold or hardware for savings; hot for trades. Never mix.
- Cap approvals to what you need. Most wallets (e.g., MetaMask) let you set a custom spending cap. Use it for stables and blue chips.
- Revoke weekly or right after you try a new DApp. I set a calendar reminder; it takes 10 minutes.
- Simulate before signing: wallets like Rabby or extensions like Wallet Guard/ScamSniffer warn on shady signatures.
- Bookmark official links. Don’t trust search ads. Many approval drains start with a typo URL.
My 10‑minute “wallet wash” once a week:
- Open De.Fi Revoke → scan all chains I use.
- Filter by unlimited approvals → revoke unknowns, old routers, dead projects.
- Check NFTs → remove setApprovalForAll to anything I’m not actively using.
- Open recent signatures in my wallet → if I see Permit/Permit2 I don’t recognize, I cut them.
- Optional: export approvals list to a note so I know what I re‑enable next week.
Real-world patterns to watch
- Fake airdrops: sites ask for a “claim” signature that’s actually Permit or setApprovalForAll. Result: stables/NFTs vanish. See recurring alerts from ScamSniffer and PeckShield.
- Imposter routers: you think you’re approving Uniswap, but it’s a lookalike contract. Always confirm the spender address on Etherscan/BscScan.
- “Gasless” signatures: harmless-looking SignTypedData popups can grant spend permissions (Permit/Permit2). If your wallet flags “Spend your USDC,” stop.
If you want the background reading: approvals explained, EIP‑2612 (Permit), and Permit2 overview. Knowing these takes you from guessing to recognizing the exact trick in front of you.
One last thing: gas costs. On mainnet, revoking a handful of approvals might cost a few dollars; on L2s it’s cents. I batch my revokes during low-gas windows and prioritize high-value tokens first.
You’re now ahead of 90% of traders who only scan and never clean. But here’s the next edge: how reliable are these scanners, where do they break, and what data do they keep when you connect? I’ll show the limits and the privacy angles next—want the honest version or the marketing one?
Accuracy, limits, pricing, and privacy
“Fast is fine—until fast gets you wrecked.” I love quick scanners, but I trust them only as far as they’ve earned it. Here’s the straight talk on what the tool nails, where it can stumble, how much it costs right now, and what happens with your data when you paste or connect.
Accuracy and false positives
The scanner leans on static checks and quick simulations. That’s great for catching the loud stuff—obvious honeypots, blacklist functions, upgradeable proxies, and owner-only switches—but any heuristic system has edge cases.
- Where it shines: Plain honeypots on EVM chains, mint functions hiding in imported libraries, owner-controlled fee changers, and classic proxy/upgrade patterns. It consistently surfaces these fast.
- Where it can miss: Exotic anti-bot code (time-based sell blocks, “max wallet” traps that only trigger on sell), obfuscated state toggles tucked behind multi-call flows, and tokens that gate selling by requiring a specific call order. I’ve seen “sell taxes” read correctly while a timed sell lock triggered later.
- Common false positive patterns:
- Upgradeable contract flagged = bad (not always). Some reputable teams run UUPS or Transparent proxies with a timelock or multisig admin. The tool can’t always verify the governance setup.
- “Can change fees” = rug (not necessarily). Many teams keep fee levers during early trading to fight MEV or bots. The flag is a risk permission, not a guaranteed abuse.
Real-world sanity check: Solidus Labs reported that hundreds of thousands of scam tokens were deployed across EVM chains in recent years, with “rug pull” patterns heavily concentrated on BSC and Ethereum memecoins. That scale means no single scanner can maintain 100% recall as scam code evolves. Use the red flags as a stop sign; use context and a small test trade if you insist on proceeding.
Trust, but verify. Every green check is a starting point, not a full stop.
Helpful habits I follow when accuracy might wobble:
- Test tiny: If everything looks fine but the token is new, I do a dust-size buy/sell to confirm transfers actually work.
- Read the wording: “Owner can change fees” or “trading can be paused” are capabilities, not outcomes. Decide if the team’s setup (docs, multisig, timelock) makes that acceptable.
Limits and coverage
No scanner covers all chains, all standards, and all off-chain context. A few practical limits I run into:
- Chain support varies: EVM is the main focus. Newer or niche chains can lag on coverage, simulators, or method decoding.
- LP locks are tricky: Lock status often depends on third-party lockers (Unicrypt, Team Finance, etc.). If the locker doesn’t leave a clean on-chain footprint or uses custom logic, the tool might not detect it. I still confirm locker addresses and lock duration on the block explorer and the locker’s page.
- Top holders aren’t always what they seem: CEX wallets and routers can dominate the holder list. The scanner can flag concentration, but it can’t always classify which addresses are operational vs. whale bags. I click through to label them manually.
- Proxy admin context: It can flag upgradeability, but determining whether the admin is a burn address, multisig, or timelock sometimes needs manual explorer work.
- New scam patterns: Fresh obfuscation, custom fee routers, or cleverly gated transfers can slip through for a bit before heuristics catch up.
If a flag affects your decision—pause, blacklist, mint, fee changer—assume it’s real until you prove it safe via explorer reads or documentation.
Pricing and access
As I write this, core web scanning is free and fast enough for day-to-day use. That’s a win.
- What’s free: Paste a contract in the browser and get a readable risk report.
- What may change: APIs, bulk scans, automation, or historical analytics may require an account or paid plan. Rate limits can apply when traffic spikes. Always check the latest details on the site.
I treat pricing like market gas fees: great when low, but I keep backups ready in case limits show up during a rush.
Data and privacy
Paste-in scans are simple: you submit a contract address, the tool analyzes code/bytecode and on-chain state, and returns a report. It’s when you connect a wallet for portfolio or revocation that you should slow down and read.
- What gets read: Balances, allowances, approvals, and positions needed to show your risks. It’s read-only unless you explicitly sign a revoke/approve/transaction.
- What gets stored: Expect standard web analytics (IP, device, cookies) and usage data tied to your wallet if you connect. Exact retention and sharing are policy-dependent—check the privacy policy for current terms.
- Your control:
- Use a fresh “scanner” wallet or a trading wallet with limited funds when connecting.
- Disable unnecessary site permissions in your browser; clear cookies if that matters to you.
- Always read the signature pop-up; “Sign to prove ownership” is fine, approvals are not. Never sign blind.
One last emotional reminder: losing funds to a malicious approval feels worse than missing a 2x. Protecting privacy and allowances is how you avoid turning a small mistake into a full drain.
So with all these caveats, where does this tool actually beat or lag others you might already know? Next, I compare it head-to-head with TokenSniffer, GoPlus, and a couple more, and show when I pick which—want the quick answer or the nuanced one?
How De.Fi Scanner compares to other popular tools
I never bet my bankroll on a single tool. Each scanner has a lens, a bias, and blind spots. Stack them right and you get a sharper picture before you press swap.
“Trust, but verify—then verify again with a second scanner.”
TokenSniffer style checks
TokenSniffer is the OG for quick EVM token sniff tests. It shines when you want an instant sniff score plus familiar red flags. Here’s how it plays with De.Fi Scanner in real trading conditions:
- Overlap that matters: both flag high buy/sell taxes, trading blocks (honeypot patterns), ownership status, and common permission risks. If both call out “can mint” or “can blacklist,” that’s a hard stop for me.
- Where TokenSniffer adds spice: the sniff score and code-similarity hints help spot copy-paste forks of previous rugs. Community notes can also provide quick context.
- Where De.Fi feels faster: the report is compact with pass/warn/fail badges, plus a one-click path to revoke approvals across your wallet. It’s the quickest “green/yellow/red” read I have open during launch season.
Real-world snap: when meme coins spike with 20–30% sell tax, both tools usually light up fees in red. That doesn’t mean “never trade,” but it does mean you size positions like they can turn on you without notice.
Quick rule I follow: if both scanners scream “no,” I close the chart and live to trade another day.
GoPlus, ScamSniffer, and block explorer sanity checks
Next layer: more angles, fewer surprises.
- GoPlus (gopluslabs.io) offers a broad risk API used by many wallets. It’s great for flags like anti-whale limits, cooldowns, trading paused, proxy status, and is source verified. If GoPlus and De.Fi both flag “upgradeable + owner control,” that’s a strong signal to rethink size or skip.
- ScamSniffer (scamsniffer.io) is my browser bodyguard. It focuses on phishing, malicious approvals, and dangerous signatures (think Permit/Permit2 drainers). It’s not a tokenomics scanner—it’s your line of defense when a DApp tries to slip in a nasty approval. Pair it with De.Fi’s revoke tool for fast cleanup.
- Block explorers (Etherscan/BSCScan) are your ground truth. Always:
- Check holders and LP token holders (is the LP burned/locked? who holds it?).
- Look for proxy contracts and who controls the proxy admin.
- Confirm source code verified and read the owner-only functions listed in the ABI.
If De.Fi flags “blacklist” or “mint,” I peek at the Write functions on the explorer to confirm the exact controls.
Case you’ll recognize: sell-blocking “honeypot” patterns like the infamous squid-themed token would have tripped basic transfer tests—scanner warnings plus a few failed sell transactions on the explorer were enough to save people pain. Different tool, same lesson: verify the path out before you go in.
When to pick which
- Speed: use De.Fi Scanner for the fastest, readable overview. It’s my first screen during new launches.
- Extra context: cross-check with TokenSniffer for its score and clone hints, and with GoPlus for structured flags (anti-whale, cooldowns, proxy, open-source).
- Phishing and approvals: keep ScamSniffer on to block drainer sites, then use De.Fi’s revoke tool regularly to clear risky allowances.
- Final step every time: confirm holders, LP status, and proxy control on Etherscan/BSCScan. Screenshots and tweets don’t lock liquidity—contracts do.
- Edge cases:
- Upgradeable contracts with anonymous teams: take warnings seriously; upgrades can rewrite the rules after you enter.
- Obfuscated or exotic mechanics: scanners may miss them; test with tiny trades and watch mempools for failed sells.
- New chains: coverage varies—expect fewer checks to pass and lean harder on explorer data.
Security firms and incident trackers keep showing the same pattern: contract risk and social engineering work hand-in-hand. A clean scan won’t save you from a malicious signature, and a safe-looking website won’t fix a mint button hiding in the owner’s toolbox. That’s why pairing tools beats perfection.
One last thought: “Don’t marry your bias—marry your checklist.” Which brings me to the questions everyone asks next—accuracy, chains, cost, and that honeypot test everyone leans on. Want the blunt answers?
FAQ: the questions people always ask about De.Fi Scanner
Quick-hit answers you can use right before you hit swap. No fluff, just what matters.
Is De.Fi Scanner safe to use?
Yes. Pasting a contract into De.Fi Scanner in your browser is safe. If you choose to connect a wallet for the revoke/portfolio features, keep a small balance, check permissions, and disconnect when you’re done.
Rule of thumb: scan with your browser, transact with a burner wallet.
How accurate is the honeypot and tax detection?
Strong for common EVM tokens, but nothing is perfect. Obfuscated code, delayed fee switches, or off-chain allowlists can sneak by any automated test. If you’re pushing forward despite risk, do a tiny live test:
- Buy a dust amount
- Try to sell it immediately
- Compare expected vs. received to gauge taxes
Example: plenty of meme launches set a high sell tax for the first blocks or until “tradingEnabled” flips. Scanners often flag “owner can change fees” or “tax > X%.” A $5 test trade can confirm before you size up.
Does Scanner show if ownership is renounced?
Yes. It also highlights powerful permissions like mint, pause, blacklist, and whether the contract is upgradeable. Watch out for a common trap: implementation ownership might be renounced, but a proxy admin can still upgrade the logic. If you see “upgradeable” plus “renounced,” it’s not truly hands-off—check who controls the proxy.
Is it free?
Core web scanning is free. Some advanced features, API access, or higher rate limits may need an account or plan—best to check current details on their site.
Which chains are supported?
Mainly EVM ecosystems (think Ethereum, BNB Smart Chain, Polygon, Arbitrum, Avalanche, and others). Coverage and depth vary by chain and change over time. If a check looks incomplete, confirm with a block explorer.
Can it detect rug pulls before they happen?
It can’t predict human behavior, but it does flag common rug vectors: unlocked LP, mint functions, blacklist/pausable transfers, owner fee controls, and upgradeability. Treat these as early warnings, not destiny. Crypto crime data (e.g., Chainalysis’ annual reports) consistently shows scams remain a major revenue source for bad actors, so any red flag deserves respect.
What should I do if Scanner flags “upgradeable contract”?
Focus on who controls the proxy admin and how upgrades are executed.
- If the proxy admin is a multisig with known signers, risk is lower
- If it’s a single EOA or unknown team, position smaller or pass
- Look for public upgrade timelocks and documented processes
Example: contracts using OpenZeppelin’s TransparentUpgradeableProxy pattern are common. That’s fine—if upgrade power is clearly governed and not a single key.
Does it replace an audit?
No. It’s a fast pre-trade filter. For larger positions, look for a reputable audit, verify that the audited commit matches the live contract, and still sanity-check permissions and liquidity.
Can I use it on mobile?
Yes. It works in mobile browsers. For revokes or portfolio views that require wallet connection, performance depends on your device and mobile wallet browser.
How do I revoke risky approvals?
Use the revoke tool linked on De.Fi’s site (or any trusted revoker) and clear anything you don’t recognize or no longer need.
- Connect the wallet with the approvals you want to manage
- Sort by risk or token value
- Revoke unlimited approvals first, then lower allowances
- Re-approve only when you’re actively using a dapp
Tip: make “weekly revoke and review” a recurring calendar event. It pays for itself the first time you avoid a drain.
What if a token shows green but still feels off?
Trust your gut. A clean score means basic checks passed, not that risk is gone. Low-liquidity pools, social engineering, or stealth team actions won’t always appear in code. If the community, comms, or liquidity setup looks sketchy, step back.
Scanner says “blacklist” or “pause” is possible—how bad is that?
Context matters. Some tokens keep these switches for launch control, then revoke them. Others use them to trap sellers or block wallets. If the team is anonymous and those powers remain, assume elevated risk until proven otherwise.
Why do scanners sometimes disagree?
Different heuristics, datasets, and network conditions. That’s normal. I like to see alignment across at least two tools. If one flags a critical permission (e.g., mint), I investigate on a block explorer regardless of what the other says.
Want a dead-simple checklist you can run in under a minute—and who should absolutely be using this tool daily? That’s coming up next. Ready for the short list that saves you from the long regrets?
My verdict, who should use it, and a simple checklist you can keep
I keep De.Fi Scanner open because it cuts through noise. In a minute or less, I get a clear read on whether a token deserves more attention or a hard pass. It’s not a lie detector, but it consistently saves me from the most common traps: honeypots, stealth mints, upgradeable proxies controlled by unknown teams, and blacklist/fee shenanigans.
In the last few weeks alone, it flagged:
- A fake stablecoin on BSC with a blacklist function and owner-controlled fees. The social hype was loud, but the scan told the real story—easy pass.
- A meme token on Base with pausable trading and a non-renounced proxy. Team was anonymous. I sized to zero.
- A “revived” coin on Ethereum that could mint beyond its declared supply. That one would have been brutal for late buyers.
Outside my own tests, independent research backs the need for this kind of first-pass filter. Reports like the Chainalysis Crypto Crime Report and scam-token studies from firms such as Solidus Labs have shown that developer-controlled permissions and token mechanics abuse remain a recurring pattern, especially on EVM chains. Tools that surface those controls fast are worth their weight in gas saved.
My rule: if the scanner screams red and I can’t immediately justify why, I move on. There’s always another chart.
Who benefits most
- Active traders who need a fast green/yellow/red read before they even open a chart.
- Newcomers who want plain-English warnings about mint, blacklist, taxes, and upgradeability.
- Anyone with DeFi exposure who wants an easy way to scan, then clean up approvals and keep risk low.
Quick pre-trade checklist
- Scan the contract on de.fi/scanner.
- If red flags like honeypot, stealth mint, or blacklist show up → pass.
- Confirm LP lock status and top holders on a block explorer and the DEX locker page.
- Cross-verify on another scanner for a second opinion.
- If any yellow flags remain, reduce size and set alerts. Consider a tiny test buy only.
- Keep approvals tight; use a revoke tool weekly or after each new DApp.
Conclusion
Use De.Fi Scanner as your first stop, not your finish line. It’s fast, readable, and ruthless about exposing the stuff that drains wallets. If a token can’t clear this first pass, it doesn’t deserve your capital or attention.
When in doubt, pass and protect your bankroll. If you want me to test a token or compare scan results, drop a note on Cryptolinks.com—happy to put tools to the test so you don’t have to.