Biggest Scams & Hacks in Cryptocurrency History

Have you ever wondered how secure your cryptocurrency investments really are? I’ve seen firsthand how the allure of crypto can sometimes lead us into murky waters. Today, let’s explore some of the most significant scams and hacks that have rocked the crypto world. Understanding these events isn’t just fascinating—it’s essential for safeguarding your own assets. Cryptocurrency offers incredible opportunities, but it also comes with risks that are often overlooked. The thought of losing your investments to scams or hacks is unsettling, and unfortunately, it’s a reality many have faced. I’ve seen how easily people can fall victim to these threats, and it’s a situation no one wants to experience. Let’s explore some of the biggest scams and hacks in crypto history so we can learn from them and take steps to protect our assets.
The Dark Side of Crypto: Why Security Matters More Than Ever
The promise of decentralized freedom is exciting, but the crypto world has also become a hotspot for cybercriminals. From exchange hacks to elaborate Ponzi schemes, investors have lost billions. The pain of seeing hard-earned money vanish overnight is something many have experienced, and it could happen to anyone.
Turning Lessons into Action: How to Protect Yourself
But it’s not all bad news. By examining these incidents, we can spot common patterns and learn how to strengthen our defenses. I’ll share insights on how to identify red flags and adopt best practices to keep your investments secure.
Why This Matters to You
Whether you’re a seasoned trader or new to the crypto scene, staying informed is your first line of defense. Let’s explore these stories together so you can navigate the crypto world with confidence.
Ready to uncover the tales of the biggest crypto heists and learn how to protect yourself? Let’s get started.

The Mt. Gox Collapse: The First Major Bitcoin Hack
Back in the early days of Bitcoin, there was one name that dominated the scene: Mt. Gox. I remember how exciting it was to see Bitcoin gaining traction, and Mt. Gox was the go-to place for trading. Handling over 70% of all Bitcoin transactions at its peak, it felt like the center of the crypto universe. But in 2014, everything changed.
What Really Happened?
The news struck like lightning—Mt. Gox had lost 850,000 Bitcoins. That’s right, 850,000 Bitcoins vanished, worth around $450 million at the time. I couldn’t believe it. How could so much just disappear?
It turns out that security lapses and possibly insider threats were at the heart of the issue. For years, hackers had been exploiting weaknesses in Mt. Gox’s systems. The exchange’s security protocols were insufficient, and there were allegations that some insiders might have been involved. Thousands of users worldwide lost their Bitcoins, and the trust we all had in the platform was shattered.
The Aftermath and Impact on Crypto Regulation
The collapse didn’t just devastate individual investors; it sent shockwaves through the entire crypto community. Governments and regulators took notice. In Japan, where Mt. Gox was based, authorities stepped in to address the lack of regulation in the crypto space.
This event prompted the introduction of new laws aimed at protecting consumers and ensuring exchanges adhered to strict security standards. It was a turning point that underscored the need for better oversight and accountability in the crypto industry. The Mt. Gox incident became a case study for why regulation, though often met with resistance, can play a crucial role in safeguarding investors.
Key Takeaways for Investors
The Mt. Gox disaster taught me some hard lessons, and I want to share them with you:
- Don’t Keep All Your Coins on Exchanges: Exchanges can be vulnerable. Consider using hardware wallets or other secure storage methods where you control the private keys.
- Do Your Homework: Before trusting an exchange, research its security measures, history, and reputation. Look for any red flags or past issues.
- Stay Informed: The crypto landscape changes rapidly. Keep up with news and updates about the platforms you use.
There’s a quote that resonates with me whenever I think about Mt. Gox:
“Trust, once lost, could not be easily found. Not in a year, perhaps not even in a lifetime.” — J.E.B. Spredemann
The Mt. Gox collapse was a stark reminder of how fragile trust can be in the digital world. It’s up to us to be vigilant and proactive in protecting our assets.
But here’s the thing—Mt. Gox was just the tip of the iceberg. Have you ever wondered what happens when the very code that powers cryptocurrencies is exploited? In the next part, we’ll explore an event that shook Ethereum and changed how we think about smart contracts forever.

The DAO Attack: Exploiting Smart Contracts
Back in 2016, I vividly recall the excitement surrounding the DAO—the Decentralized Autonomous Organization that was supposed to revolutionize how we think about corporate governance. It was a groundbreaking experiment, but then the unthinkable happened: hackers exploited a vulnerability and siphoned off $60 million worth of Ether. It was as if someone pulled the rug out from under the entire Ethereum community.
“In the world of crypto, a single flaw in code can undermine even the most ambitious projects.”
Understanding the Vulnerability
So, how did this all go down? The DAO’s smart contract had a loophole—a “recursive call” vulnerability. Imagine having a bank account that lets you withdraw money multiple times before the balance updates. That’s essentially what the hackers did. They kept requesting funds before the contract could record the withdrawal, allowing them to drain the DAO’s funds systematically.
This wasn’t just a minor glitch; it was a fundamental flaw that exposed the risks inherent in smart contracts. It taught us that while code can execute agreements flawlessly, it can also blindly follow flawed instructions, leading to catastrophic outcomes.
Hard Fork: Ethereum’s Response
The fallout sparked intense debate within the Ethereum community. Should the blockchain remain immutable, honoring the “code is law” principle, or should they intervene to rectify the wrong? Ultimately, a hard fork was implemented. This split the Ethereum blockchain into two: Ethereum (ETH), which reversed the hack to return the stolen funds, and Ethereum Classic (ETC), which upheld the original ledger.
This decision wasn’t taken lightly. It raised critical questions about decentralization and governance. Was altering the blockchain setting a dangerous precedent? Or was it a necessary step to protect the community? The split highlighted the delicate balance between upholding principles and adapting to unforeseen crises.
What This Means for Smart Contract Security
The DAO attack was a stark lesson in the importance of robust security. It became clear that smart contracts need rigorous auditing before deployment. Just like we wouldn’t live in a house built on a shaky foundation, we shouldn’t trust our assets to unverified code.
Since then, the industry has placed a greater emphasis on:
- Code Audits: Independent reviews to catch vulnerabilities.
- Formal Verification: Mathematical proofs to ensure code behaves as intended.
- Bug Bounties: Incentivizing ethical hackers to find flaws before malicious actors do.
The takeaway? Security isn’t an add-on; it’s an integral part of developing smart contracts. We must prioritize it at every step to protect not just individual projects but the integrity of the blockchain ecosystem as a whole.
The DAO incident wasn’t just a setback; it was a turning point. It forced us to confront the imperfections in our systems and spurred improvements that have strengthened the crypto world. But as we’ll see, even with these hard-earned lessons, new challenges continue to emerge. Ever wondered how these events have shaped the security measures of today’s major exchanges?
The Coincheck Hack: A Wake-Up Call for Exchanges
Back in 2018, the crypto world was rattled when Coincheck, one of Japan’s largest cryptocurrency exchanges, was hacked. Over $530 million worth of NEM tokens vanished overnight, marking one of the biggest heists in digital currency history.
How the Hack Occurred
So, how did this happen? Coincheck made a critical mistake by storing a vast amount of NEM tokens in a hot wallet—that is, a wallet connected to the internet. But it wasn’t just that. The assets weren’t properly encrypted, leaving a door wide open for hackers.
Imagine leaving your front door unlocked in a neighborhood known for break-ins. It sounds unthinkable, right? Yet, that’s essentially what Coincheck did on a much grander scale. The lack of basic security measures not only cost them financially but also eroded user trust.
Regulatory Repercussions in Japan
This wasn’t just a blow to Coincheck; it shook the entire Japanese crypto industry. The Japanese Financial Services Agency (FSA) couldn’t sit back and watch. They stepped in with a tighter regulatory grip, implementing stricter guidelines for all exchanges operating in the country.
These new regulations weren’t just red tape. They were necessary actions to protect consumers and restore faith in the burgeoning crypto market. Exchanges were now required to:
- Enhance their security protocols
- Conduct regular audits
- Comply with more rigorous reporting standards
The Coincheck incident became a catalyst for change, pushing both exchanges and regulators to prioritize security like never before.
Steps Exchanges Must Take to Secure Assets
So, what’s the lesson here? For exchanges, it’s a stark reminder that security can’t be an afterthought. Here are some best practices that need to be the norm:
- Cold Storage Solutions: Storing the majority of assets offline to protect against online threats.
- Multi-Signature Authentication: Requiring multiple approvals for transactions adds an extra layer of security.
- Regular Security Audits: Ongoing assessments to identify and fix vulnerabilities.
- Employee Training: Ensuring staff are educated about security protocols to prevent insider threats.
As the saying goes, “An ounce of prevention is worth a pound of cure.” In the crypto world, proactive security measures aren’t just wise—they’re essential.
Feeling Secure in a Vulnerable World
Events like the Coincheck hack can make anyone feel uneasy about diving into crypto. Trust me, I get it. It’s like hearing about a bank robbery and wondering if your money is safe. But don’t let fear hold you back from exploring the potential that cryptocurrency offers.
By understanding these incidents, we’re not just spectators—we’re becoming smarter, more vigilant participants in the crypto space. After all, knowledge isn’t just power; it’s protection.
Curious about how other major exchanges handled their security breaches? Let’s check out the next story that shook the crypto community and see what lessons we can learn.
The Bitfinex Breach: High-Tech Theft
I still remember the shockwaves that rippled through the crypto community in 2016 when Bitfinex, one of the largest exchanges at the time, announced it had been hacked. Approximately 120,000 Bitcoins vanished overnight, amounting to a loss of around $72 million back then. It wasn’t just another hack; it was a sophisticated assault that targeted the very mechanisms we thought were safe.
Examining the Attack Vector
You might be wondering how something like this could happen to a major exchange. Bitfinex was using multi-signature wallets provided by BitGo, which were supposed to add an extra layer of security. But the hackers found a way to trick the system.
They exploited vulnerabilities in the exchange’s security protocols, specifically targeting the way Bitfinex handled their multi-signature transactions. By manipulating these weaknesses, the attackers authorized withdrawals that shouldn’t have been possible. It was a stark reminder that even advanced security measures aren’t foolproof if not implemented correctly.
Bitfinex’s Recovery Plan
The aftermath was chaotic. Users were panicking, and trust in the platform plummeted. But Bitfinex took an unconventional route to address the crisis. They issued a token called BFX to the affected users, representing their lost funds. Essentially, they turned the debt into a kind of investment.
Over time, Bitfinex bought back these tokens, gradually repaying the victims. By April 2017, they announced that all the BFX tokens had been redeemed. It was a bold move that showed commitment to their users, but not everyone was satisfied. The incident left a lasting scar on the community’s perception of exchange security.
Investor Confidence and Exchange Trustworthiness
This breach wasn’t just about the loss of funds; it struck at the heart of trust between exchanges and their users. We place a lot of faith in these platforms to safeguard our assets, and when that trust is broken, it’s hard to rebuild.
Transparency became a buzzword after the Bitfinex hack. Investors started demanding more openness about security practices and financial health. Exchanges that prioritized communication and rigorous security protocols stood out from the rest.
As the saying goes, “Trust takes years to build, seconds to break, and forever to repair.” This couldn’t be truer in the crypto world. We need to hold exchanges to higher standards because, at the end of the day, it’s our money on the line.
So, how can we navigate this landscape where even the giants can fall? Is there a way to safeguard ourselves against these unforeseen catastrophes?

The Poly Network Exploit: When Hackers Return Funds
Imagine waking up to discover that over $610 million in cryptocurrency has been stolen, only to find out later that the thief decides to give it all back. Sounds unbelievable, right? That’s exactly what happened with the Poly Network exploit in 2021. This incident didn’t just shock the crypto community—it left us all questioning the very nature of security and trust in decentralized finance (DeFi).
Anatomy of the Exploit
So, how did this colossal breach occur? The attacker took advantage of vulnerabilities in Poly Network’s cross-chain interoperability protocols. Essentially, they found a way to manipulate the smart contracts that allow different blockchains to communicate and transfer assets.
By exploiting a flaw in the verification process of contract calls between chains, the hacker was able to trick the system into approving massive transfers to their own wallets. It’s like discovering a loophole in a bank’s security system that lets you withdraw unlimited cash without setting off any alarms.
The Hacker’s Motives and Actions
But here’s where the story takes an unexpected turn. Instead of vanishing into the digital shadows, the hacker started communicating with Poly Network and the public. Through embedded messages in Ethereum transactions, they claimed to have carried out the hack “for fun” and to expose the vulnerability before others could exploit it.
“I am not very interested in money,” the hacker wrote, sparking a whirlwind of speculation about their true intentions.
Over the next few days, a dialogue unfolded between the hacker and Poly Network. In a surprising move, the hacker began returning the stolen funds. They even accepted an offer from Poly Network to become their Chief Security Advisor, highlighting a bizarre but fascinating twist in the narrative.
Strengthening DeFi Security
This incident shines a light on some glaring security challenges within DeFi platforms. If a major player like Poly Network can be exploited, it raises concerns about the robustness of smart contracts and cross-chain protocols across the industry.
So, what can we learn from this? Here are a few takeaways:
- Rigorous Code Audits: Regular and thorough audits by reputable security firms are a must. This helps catch vulnerabilities before they can be exploited.
- Bug Bounty Programs: Encouraging ethical hackers to find and report bugs through incentives can turn potential threats into opportunities for improvement.
- Transparent Communication: Open dialogues between platforms and their communities build trust and can lead to collective problem-solving.
The Poly Network exploit was a wake-up call that, despite the innovative nature of DeFi, we can’t overlook security fundamentals. It also showed that sometimes, even in the wild west of crypto, unexpected alliances can form to strengthen the ecosystem.
But this isn’t the end of the story. What happens when an exchange not only collapses due to internal issues but is also hit by a mysterious hack afterward? There’s more to uncover in the complex world of crypto security.

The FTX Collapse and Subsequent Hack: A Modern Cautionary Tale
In 2022, we witnessed something that shook the crypto world to its core. FTX, a platform many of us trusted and perhaps even used daily, spiraled into bankruptcy amid serious allegations of mismanagement. Just when we thought the dust was settling, a mysterious hack drained funds from the platform, leaving users in a state of panic.
Unpacking the FTX Downfall
So, how did things go so wrong for FTX? It turns out that behind the sleek interface and impressive marketing, there were underlying issues. Reports started emerging about financial irregularities, such as questionable lending practices and insufficient reserves to cover user assets. This led to a massive loss of confidence among investors and users alike. People rushed to withdraw their funds, but for many, it was too late. The liquidity just wasn’t there.
The Mysterious Hack After Bankruptcy
As if the collapse wasn’t chaotic enough, news broke of an unauthorized transfer of funds from FTX’s wallets. Over $400 million worth of cryptocurrencies vanished in what the company described as a hack. The timing couldn’t have been worse—or more suspicious. Users were left wondering whether this was an external attack or an inside job. The lack of clear communication from FTX only added to the confusion and mistrust.
Legal and Ethical Implications
The fallout from FTX’s collapse and the subsequent hack has caught the attention of regulators worldwide. There are ongoing investigations into what went wrong and who should be held accountable. This situation has spurred discussions about tightening regulations for crypto exchanges to protect users. It’s a complex debate—how do we preserve the decentralized spirit of crypto while ensuring transparency and security?
The FTX debacle is more than just a news headline; it’s a wake-up call for all of us involved in the crypto space. It raises pressing questions about trust, security, and the measures we need to take to safeguard our assets. But what’s the path forward from here?
Other Cryptocurrency Scams and Schemes
Cryptocurrencies are an emerging field. It takes time for the level of knowledge from the side of consumers to catch up with the risks that circulate. Not only is it an emerging field but it also deals in the field of digital and sometimes anonymous money. This makes it a ripe place for hackers and scammers alike. The first step to help prevent against being hacked or scammed is to be aware of what has happened in the past. We cover the major scams which have taken place to date.

The Exchange Risk – Mt. Gox
The biggest hack in the history of cryptocurrency occurred in 2014 when Mt. Gox had over 740,000 Bitcoin stolen from the exchange. It is common advice in cryptocurrencies not to leave your funds on an exchange and this hack is still referred to today. When users store their funds on exchanges, they are handing over the control of their funds to the exchange.
At the time of the hack, Mt.Gox was handling over 70% of the transaction volume occurring in Bitcoin. Users who had their funds hacked still have not received any compensation back despite the value of Bitcoin drastically rising since the time of the hack.
Since this time, there have been numerous more exchange hacks with Bitfinex being another notable hack. It is always important to remember that leaving your funds on an exchange exposes your funds to this type of risk.
The Too Good to be True – Bitconnect
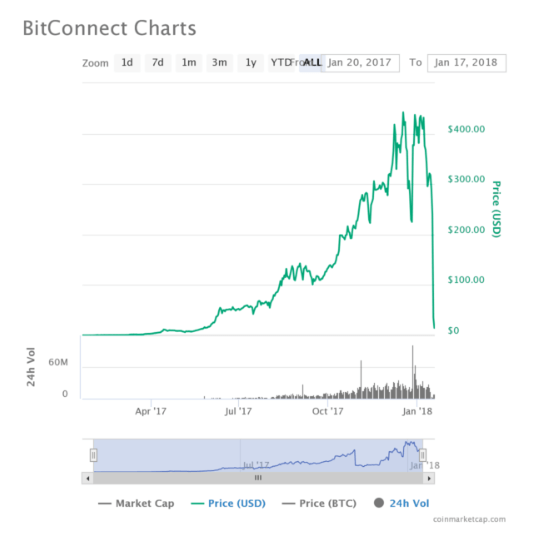
A more recent scam was peer-to-peer lending platform Bitconnect. The cryptocurrency gained huge amounts of attention before finally being revealed to be a scam. Many were aware it was a scam prior to it collapsing but there was also large support behind Bitconnect from investors.
The cryptocurrency promised returns based on peer-to-peer lending. Bitconnect guaranteed investors 1% daily compounded returns. In late 2017 and early 2018, the company faced legal troubles which led to the price of the cryptocurrency crashing.
Bitconnect was structured as a Ponzi scheme with the price of the cryptocurrency depending on new investor capital arriving. It is important to be aware of this scam in cryptocurrencies as others operate in the same manner. Cryptocurrencies such as Onecoin have been organised in the same structure as a Ponzi scheme. The general rule of thumb is if it is too good to be true, it probably is.
ICO Scams – Plexcoin
Initial Coin Offerings (ICOs) exploded in 2017. ICOs are a new fundraising mechanism whereby teams raise funds via distributing a cryptocurrency or token related to a project they plan to develop. If the project gets successfully developed, investors hope that the token they invested in will be worth far more.
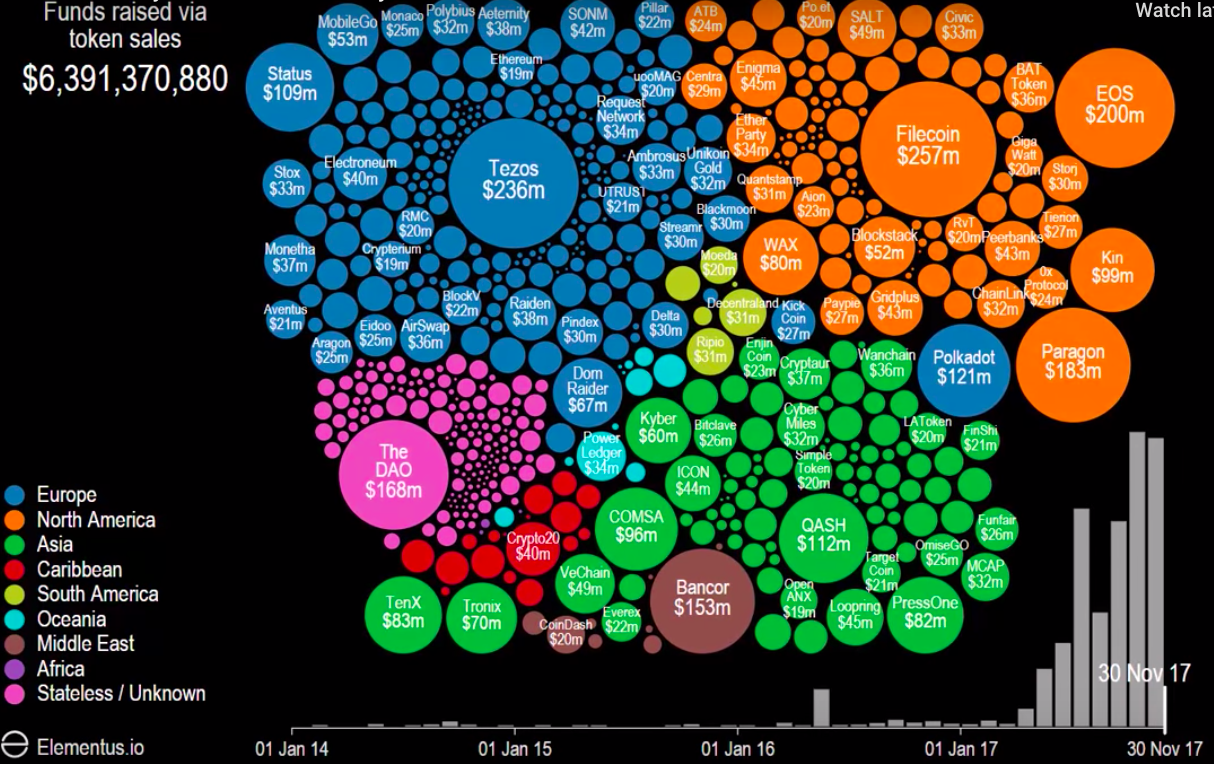
The growing number of ICO’s has resulted in there also is a growing number of ICO’s which are scams. There have been countless exit scams where ICOs were completed and the team disappeared afterwards. All the proper channels are typically set up such as a Telegram to help investors contribute and fake LinkedIn profiles to represent the team.
There are often signs when an ICO is going to be a scam. The fraudulent Plexcoin ICO promised investors an over 1300% return in 29 days. The project raised approximately $15 million from investors and the founders behind the project have since received sanctions from the United States SEC. In many of these scenarios, the team behind the project is unknown and disappear after the ICO is complete.
Send 1 ETH, Get 2 Back – Vitalik Non-Giver of Eth
This is one of the more common scams and is still prevalent. The scam is based on enticing individuals to send cryptocurrency in hopes to receive a greater amount in return. So many people have got caught by this scam that innovators and influencers such as Vitalik Buterin have changed their social media names to explicitly state that they are not giving away Ethereum. Scammers will still post trying to entice users to send cryptocurrency.
It is estimated that approximately $1.5 million has been scammed from enticing users to send cryptocurrencies.
Protecting the Private Key and Checking the Public Key
It is common advice in cryptocurrencies to closely protect your private key. Revealing your private key to anybody provides access to the funds in the wallet. By putting your private key into shared databases or cloud services, you are running the risk of this information being accessed by someone else and losing your funds.
Scams have also been created targeting the public key. When you are sending funds, you need to know the recipient’s public address. One piece of malware changes the user’s address when you copy it to the clipboard to another address. When you go to paste the address, the scammer’s address will be pasted instead and the funds will go to the wrong account. This emphasises the need to always double check the address when sending funds. There are no estimates for how much has been lost through private key and public key scams and hacks but it is certainly an enormous amount.
After seeing how easily the crypto landscape can shift, it’s more important than ever to protect ourselves. The opportunities are vast, but so are the risks. Let’s take a proactive approach to secure our investments and make informed decisions.
Protecting Yourself Against Scams and Hacks
First things first—security starts with us. Here are some practical steps I’ve found invaluable:
- Use Hardware Wallets: Storing your cryptocurrencies offline in hardware wallets adds an extra layer of security that’s hard to beat.
- Enable Two-Factor Authentication (2FA): Whenever possible, activate 2FA on your exchange accounts to prevent unauthorized access.
- Stay Informed: Keep up with the latest news and be aware of potential threats. Knowledge is power in staying ahead of scammers.
- Verify Before You Trust: Always double-check URLs and be cautious of unsolicited messages or emails asking for personal information.
- Backup Your Keys: Securely back up your private keys and seed phrases. Losing them can mean losing access to your assets forever.
The Role of Privacy Coins in Security
Privacy-focused cryptocurrencies like Monero (XMR) offer enhanced anonymity for transactions. While they can be a tool for privacy, it’s essential to use them responsibly.
These coins use advanced cryptography to obscure transaction details, which can protect you from potential targeting by bad actors. However, regulatory scrutiny around privacy coins is increasing, so it’s wise to stay updated on the legal landscape in your region.
Building a Secure Crypto Future
We all have a part to play in making the crypto space safer. Here’s how we can contribute:
- Advocate for Better Security Practices: Support platforms and projects that prioritize robust security measures.
- Demand Transparency: Choose exchanges and services that are open about their security protocols and audits.
- Educate Others: Share your knowledge with friends and family who are interested in crypto to help them avoid common pitfalls.
- Participate in the Community: Engage in discussions and provide feedback to projects to foster accountability.
Final Thoughts: Empowering Yourself Through Knowledge
The crypto world is exciting, but it’s not without its challenges. By learning from past events and taking deliberate steps to protect ourselves, we can navigate this landscape with confidence.
Remember, staying vigilant and informed isn’t just about safeguarding your assets—it’s about contributing to a stronger, more secure crypto community for all of us.

