Crypto Security Guide Updated: Everything You Need to Do to Secure Crypto Investments

As exemplified by the growing demand for crypto, it is becoming fashionable to own digital assets as a hedge against inflation or purely for investment purposes. While this is a welcomed development, it does not tell the full story of the extra security responsibilities that comes with investing in cryptocurrencies, especially when you plan on purchasing and holding coins.
Intending crypto investors must take into account a long list of factors and adopt standard security measures to ensure that they are not exposed to unforeseen threats. In this guide, I will discuss all of the security measures that you should consider as a crypto investor and how to implement them.

Common Security Issues Investors Face
When it comes to crypto security, the threats out there can feel overwhelming. The most painful part? Many investors fall victim to the same mistakes over and over again. Let’s break down the top security risks that investors face every day.
Phishing Scams and Social Engineering Attacks
Phishing scams are the cybercriminal’s favorite trick. Here’s how they often work: You receive an email or message that looks like it’s from your wallet provider or exchange. It leads you to a perfect replica of their website, where you’re asked to log in. Once you do, your credentials – and potentially your funds – are gone.
For example, in 2022, a phishing attack targeted MetaMask users with a fake “update your wallet” email. Thousands fell for it, losing access to their wallets in minutes. Always check the URL and never click on random email links. Bookmark official sites and verify links on legitimate sources, not through social media messages.
Poor Storage Practices
Storing your crypto funds on an exchange for convenience might seem easy, but it’s one of the riskiest moves you can make. Why? Because exchanges are prime targets for hackers. Just look at the infamous Coincheck hack in 2018 – over $500 million in assets were stolen from the platform.
Don’t let this happen to you. Ensure you’re moving your funds to private wallets, and when appropriate, consider cold wallet storage (we’ll explore this more in upcoming sections).
Lack of Understanding of Security Tools
Here’s a scenario: You hear about two-factor authentication (2FA) but don’t set it up because it seems like a hassle. Maybe you’re unsure how encryption works, so you don’t bother encrypting sensitive data. Unfortunately, this lack of knowledge can make you extremely vulnerable.
In one recent survey, 38% of crypto holders admitted they didn’t use 2FA or proper security measures when securing their accounts. Let that sink in for a moment. Tools like hardware wallets, 2FA apps, and encrypted storage options are some of the easiest defenses you can use – and they’re incredibly effective when done right.
The Emotional Side of Losses
Losing your crypto isn’t just stressful. It can be emotionally devastating. Imagine logging into your account to find your life savings gone because of a mistake or hack. For some, the financial blow is minor compared to the emotional toll of knowing it could’ve been prevented. This is why security isn’t a luxury – it’s a necessity.
The good news is that with the right mindset and practices, you can sleep peacefully knowing your investments are protected. But this brings up an important question: What’s changing in 2023 that makes security even more critical? Let’s see how the landscape is evolving in surprising ways.

What Are Digital Asset Wallets?
Digital assets or cryptocurrencies are simply virtual assets powered by blockchain technology. The blockchain or distributed ledger records and confirms the transactions executed using these digital assets, and in essence, eliminates the need for banks of third parties. These currencies do not have a physical form. Hence, they require sophisticated security systems. So, how do you secure an asset that technically does not exist physically and cannot be stored in vaults like cash or precious metals? The answer is cryptography.
By incorporating cryptography in blockchain technology, it becomes possible to assign two sets of keys which serve as a form of establishing the ownership of coins as well as encrypting and decrypting transactions or information. Called Private and public keys, these cryptographic keys are long strings of alphanumeric characters that ensure that only authorized entities have access to coins just like how account names and passwords function in the banking world. Think of it as a system similar to conventional banking methods, where you have to enter the bank account details of the recipient and confirm the transactions by inputting your password
Going by this analogy, we can say that private keys share the same level of sensitivity as bank passwords because they are used to sign transactions and decrypt the incoming funds. On the other hand, public keys are blockchain iterations of account names and numbers, which also encrypt outgoing transactions. To successfully send crypto, you must include the public key of the recipient to encrypt the transaction, and the receiver must use the corresponding private key to decrypt it to receive the funds.
However, unlike traditional banking systems, it is not an actual exchange of coins that defines blockchain transactions. What happens is that the blockchain only records the transfer of ownership of coins. As such, when you execute transactions on the blockchain you are not transferring funds.
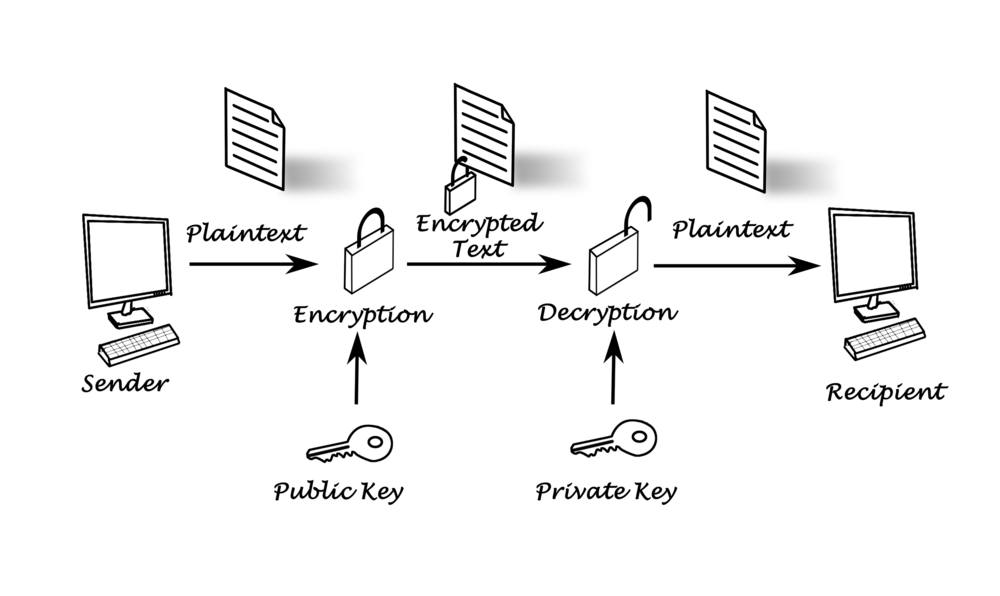
Due to this framework, private and public keys are essential components of blockchain security because they help ascertain the ownership of cryptocurrencies and authorize users to execute transactions. And so, it made sense to create security infrastructures designed to store these sensitive keys. Herein lies the motivation for introducing cryptocurrency wallets.
Therefore, contrary to popular belief, digital wallets do not store cryptocurrencies. Instead, they provide the appropriate storage for private and public keys. Also, note that wallet addresses are just hashed public keys. Simply put, wallet addresses are shortened versions of public keys. And as highlighted earlier, cryptocurrency wallets only alter crypto balances based on the change of ownership of cryptocurrencies. If you lose access to your private key, there is little or no chance of recovering your coins. Also, unlike conventional financial systems, it is difficult to reverse transactions and even harder to recover stolen coins. Hence, you must do all you can to secure your wallets.
What Are the Classes of Crypto Wallets?
Now that you understand the fundamental of crypto wallets, it is imperative to explore the appropriate security systems. But first, let us discuss the various classes of wallets and the factors that you should consider before opting for one. There is more than one way to classify crypto wallets. You can base the classification on the level of autonomy they provide or the nature of their connectivity to the internet. The former categorizes wallets as custodial or non-custodial, while the latter discusses the hot and cold wallet classification.
What Are Custodial and Non-Custodial Crypto Wallets?
Some wallets offer full autonomy to users by providing them with the tools they need to store their private keys and public keys. In that way, crypto holders have full control over their digital assets, and they are tasked with the responsibility of securing them. Crypto wallets that fall under this category are what we call non-custodial wallets. While this is a given, there is another variation, which stores the private keys on behalf of users. The crypto holder does not have a complete say over their assets because they utilize a custodial-based system of wallet service.
Custodial Wallets VS Non-Custodial Wallets
When comparing custodial and non-custodial wallets, it is not enough to just base your decision on the fact that one offers autonomy and the other doesn’t. Although non-custodial iterations of digital asset wallets are somewhat popular in the crypto community, they may not suit your type of crypto venture. As quality crypto custodial solutions continue to emerge and incorporate standard practices like insurance, you might find that it is safer to rid yourself of the responsibility of safeguarding your private keys. Hence, you have to take the time to analyze the best variant of wallet that suits your business or investment venture.
However, if we are to base this comparison on present factors, it is safe to say that non-custodial wallets are way more secure than the custodial counterparts. The moment you outsource the storage of your private key, then the coins linked to your public address are technically not yours. Events beyond your control can cause the permanent loss of your crypto holdings.
This brings us to the second classification which describes wallets as being hot or cold.
What Is A Hot Wallet?
As its name implies, a Hot wallet is a cloud-based digital asset storage infrastructure that is connected to the internet. This wallet framework is always available to users and permits instant transactions as the keys are stored in the cloud. Also, some variants of cold wallets utilize custodial-based infrastructures. Hence, you have little say about what happens to your wallet, and you have to adhere to the policies of the wallet provider. Note that all software solutions, including desktop wallets, mobile wallets, and web wallets fall under this category.
What Are Cold Wallets?
In contrast to hot wallets, cold wallets allow users to store their private keys in an offline environment. Hence, you have to interface the wallet with software to execute transactions. Due to the offline nature of these wallet iterations, they provide more protection against hacks or other threats on the internet. Naturally, most cold wallets offer a non-custodial framework. The only exceptions are the new crop of custodial services that present users with the option of a cold storage system. The types of wallets that are prominently referred to as cold wallets are paper wallets and hardware wallets. The latter are advanced USB drive sticks designed to store private keys offline.
Cold Wallet VS Hot Wallet
Owing to the recurring security hacks associated with hot wallets, it is advisable to opt for cold wallets. In this way, you eliminate counterpart risks that may potentially cost you the entirety of your funds. It also reduces the possibility of losing your coins because of computing failure caused by viruses or other malicious software.
Nonetheless, these arguments do not absorb cold wallets of their apparent disadvantage. For one, it is not suitable for frequent usage. In other words, it is not the ideal wallet solution for individuals who are likely to execute transactions frequently. For such individuals, it is best to utilize both types of wallets. I advise that you store the bulk of your funds in a cold wallet while you transfer a small percentage to a hot wallet for trading on exchanges or executing instant transactions.

Factors to Consider When Choosing A Wallet
For a more comprehensive article on how to handpick the best digital asset wallets based on other factors, you can check the top cryptocurrency wallet guide on Cryptolinks. Here, I will focus on the security aspect of this topic. You should take into account the following before you choose a wallet.
The Type of Cryptocurrency You Intend Buying and Owning
I am sure that you know by now that there are over 6000 cryptocurrencies and tokens available in the crypto market. And for new investors, it is important to ascertain that the wallet you are considering supports the crypto you want to buy. Compatibility is a very vital factor when choosing digital wallets.
The Number of Cryptocurrencies You Plan on Purchasing
For those interested in buying more than one coin, it is crucial to decide whether you want to have all your coin in a single wallet platform or store them separately. Your decision will determine if you should go for a multicurrency digital asset wallet or opt for a separate wallet for each. Also, when a wallet provider promises multicurrency features, you should take the time to research the proficiency of the wallet in delivering industry-standard security for each supported coin.
The Volume of Cryptocurrency and The Type of Crypto Activity
The more cryptocurrency you are looking to buy, the more it is advisable to explore a broad range of security implementations. You ought to decide if a custodial or a non-custodial wallet is the most suitable. Also, depending on the type of activities you are looking to engage in, you may have to use both. Hence, you ought to identify the basic requirements of your crypto activities as well as the security threats attributed to them.
Two-Factor Authentication
Apart from the username and password layer of protection, your wallet provider must include another layer that authenticates users’ identity whenever they want to sign in to the wallet, access sensitive information, or transfer funds. This second layer of security is called the two-factor authentication of 2-FA. With this system, you can set a biometrics verification process as another security shield or simply have the wallet send and request for OTP codes before executing certain commands. With this, it is less likely to fall victim to thefts or unauthorized access even when your password is compromised.
The Reputation of The Wallet Provider
When in doubt, the easiest option is to research the wallet provider’s reputation, especially regarding security. Things to look out for include the milestones achieved security-wise, the provider’s level of commitment to security, the infrastructures provided for users’ safety, and so on. More importantly, you should ascertain that the wallet provider has maintained a flawless security record.

Crypto Wallet Security Tips
Below are some of the crypto wallet security tips that you should consider.
Encrypt Your Wallet
It is advisable to encrypt your wallet such that it becomes impossible for bad actors to spend or transfer your coins, even when they breach the primary security system of your wallet. The process of encrypting wallets is somewhat straightforward as a majority of wallets provide in-built encryption features for this process. For a desktop wallet, you may need to generate a passphrase to encrypt your wallet. By doing so, everyone that has access to the wallet is restricted to a spectator-only mode. They can track transactions but cannot execute them unless they enter the passphrase. Note that you may have to input the passphrase manually whenever you want to transfer funds.
You can also encrypt your mobile wallets. However, unlike the process involved in encrypting desktop wallets, mobile wallets use pin codes for encryption. Therefore, you only need to enter a pin to sign transactions.
Backup Your Wallet
Other than encryption, you can also backup your wallet for added protection against permanent loss. This security measure is vital because it offers the opportunity of recovering private keys if you lose your phone or computer. To backup your wallet, all you need to do is find within the wallet software an option to generate a seed phrase. The seed phrase is a list of random words, which you can use to recover a lost wallet. Once you generate the seed phrase, it is vital to store it in a secure location. You can either write it down on paper and keep it securely or export it to a dedicated external device. You can automatically recover your wallet by entering this seed phrase into a new wallet.
For those who had opted to store their seed phrase online or on a device that is connected to the internet, it is advisable to encrypt the private key or the seed phrase. You can also decide to use several locations to prevent a single point of failure. When you distribute your seed phrase, your backup becomes less susceptible to coordinated attacks.
Use A Strong Password
Since your wallet is a sensitive account, you ought to ensure that you use a strong password as the first layer of protection. Ensure that the password is long, unique, and unrecognizable. Even, you can go as far as to use a password generator.
Regardless of the method you use to generate your password, you must try as much as possible to memorize them. Depending on the type of wallet you opt for, you may lose access to your coin permanently when you forget your password. In this case, it is better to write down your password and keep it in a vault. This approach is vital for individuals looking to store their coins in an offline wallet for a long duration.
Sign Transactions Offline
You can capitalize on the strengths of both wallet frameworks to great effects. All you need to do is have offline and online computers sharing components of a single wallet. With this, you can store your private key on a cold wallet and track activities via the hot wallet. To issue transactions, you will have to create a transaction on the internet-enabled computer, transfer it via USB to the offline computer and sign it with your private key. Once this is done, you will need to send the signed transaction back to the connected system.
Use Two-Factor Authentication
As mentioned earlier, 2-FA is a standard security system that we expect every wallet service to provide. The unavailability of 2-FA restricts users to a single layer of protection, which is often easy to bridge. Also, note that a majority of wallet providers enable 2-FA as an optional security feature. Hence, the onus is on you to activate it and pick the mode of authentication you prefer.
Use Multi-Signature
A multi-signature or multi-sig infrastructure uses a security system that requires two or more signatures or private keys to execute critical operations. That way, a multi-sig wallet will only confirm transactions when all authorized users of the account input their private keys. Simply put, a multi-sig wallet allows multiple individuals or entities to run a single account. Therefore, all authorized users of a single wallet must input their signature to transfer funds.
Update Your Software
When you have a wallet on your device, it becomes critical to update the operating system and other vital software. This practice will ensure that your computer or mobile device is not susceptible to hacks. Also, you should the same for your wallet’s software. By keeping the software up to date, you can ascertain that you are implementing the wallet provider’s latest security upgrades that can defend against new security threats.
Confirm Wallet Addresses
Since it is almost impossible to recover funds, it is advisable to double-check recipients’ public addresses before transferring funds. This will prevent you from sending funds to the wrong address. You can also copy and paste addresses or use QR codes to limit the chances of errors.
Be Discrete
One thing many fail to understand is that a majority of blockchains do not guarantee the anonymity of users. Instead, the system offers a pseudonymous approach where the identity of users is represented by aliases or public addresses. Blockchain like Bitcoin and Ethereum use a public ledger to record transactions and this framework allows other network participants to track the activities of each address. Users lose any form of privacy they thought they have once it becomes possible to link addresses to users’ real identities. Thus, it is not wise to post your wallet addresses online. Such a careless move may provide bad actors with all the information they need to track your crypto activities and uncover your digital wealth. Do not put a target on your back by being ignorant of the threats lurking on the internet.
Unless you have encrypted your wallet, it is a bad idea to store your private keys on a public device. It is also inadvisable to run your wallet on a shared computer. You should always use a private device to access your wallets. if possible, you could utilize a dedicated device for added protection against unauthorized access.
Having exhausted the crypto wallet security discussion, the next section highlights critical crypto exchange security tips.

Best Practices to Secure Your Crypto Investments
The crypto space is exciting: fast-paced, packed with opportunities, and frankly, a little nerve-wracking at times. But as thrilling as it is to watch your portfolio grow, one careless mistake could wipe it all out. Don’t let avoidable blunders erase what you’ve worked so hard for. With a few solid habits, you can shield your digital assets and sleep a little easier at night.
Seed Phrases: What You Must Know
No matter where you are on your crypto journey, understanding the importance of your seed phrase is critical. Think of it as the master key to your entire digital kingdom. Here’s a fact: if someone gets a hold of your seed phrase, they’ve got full access to your funds. Let that sink in.
What’s the right way to handle your seed phrase?
- Never store it online: Text documents, cloud storage, or even screenshots on your phone are risky. Hackers can exploit these loopholes.
- Use physical backups: Write it down on paper (yes, good old-fashioned pen and paper). Better yet, create multiple paper copies and store them in different safe spots.
- Consider metal backups: For extra protection against fire, water, or wear and tear, tools like engraved steel plates are a great option.
Here’s a mistake I’ve seen way too often: People think seed phrases are just another “password.” No, they’re far more powerful. A leaked password might require some damage control. A leaked seed phrase? You’re likely out of luck.
“Security is not a product, but a process.” – Bruce Schneier
Avoid Reusing Passwords
We all love taking shortcuts – reusing passwords feels easier and less stressful, right? But this habit could be one of the most dangerous. Cybercriminals count on laziness, and password reuse makes their job easier.
Here’s a real-world example. Ever heard of the “credential stuffing” attacks? Hackers use stolen login info from one platform (e.g., a hacked email account) to try and gain access to another (like your crypto exchange). If you’re guilty of recycling passwords, you’re practically holding the door open for them.
Strong passwords must be:
- Unique: Different for every platform or wallet.
- Long: At least 12 characters, using a mix of letters, numbers, and symbols.
- Managed wisely: With a reliable password manager (I talked about these earlier – they’re a lifesaver).
A great password doesn’t just protect your funds, it also secures your peace of mind. And peace of mind? That’s priceless.
Double-Check Transaction Details
Imagine this: You’re sending $500 worth of Bitcoin, your hands are shaking, and in the rush, you mistype the recipient address. That money is gone forever. There’s no “undo” button or customer support hotline in crypto. Every transaction is final.
How do you avoid this nightmare?
- Copy-paste carefully: Always double-check the wallet address before hitting send. Scams like “clipboard hacking” can alter text in your clipboard if your system is compromised.
- Do a small test transaction: Before transferring a large amount, send a tiny amount first to ensure the address is correct and functional.
- Check transaction fees: Mistakes can happen here too. Sending too low of a fee can mean delayed transactions, while extremely high fees can cost you unnecessarily.
I personally make it a habit to check, re-check, and even triple-check addresses and details. It may feel slow at first, but when you realize what’s at stake, you’ll thank yourself every time you’re extra cautious.
Ultimately, the small, consistent habits are the ones that make the biggest difference. Let me ask you this: Have you ever thought about when it’s the right time to move your hard-earned crypto off an exchange into a safer storage solution? There’s a reason everyone calls it the golden rule of crypto investing. Curious? I’ll explain everything in the next section.

When and How to Use Cold Wallet Storage
It’s often said, “Not your keys, not your coins.” Honestly, this might be the most crucial advice you’ll ever hear when it comes to protecting your cryptocurrency investments. If your funds are sitting on an exchange or in some hot wallet, let’s face it – they’re at risk. Hackers, exchange freezes, and even plain old negligence can strip you of everything. But here’s the good news: cold wallets exist, and they’re the ultimate shield if used right.
What Exactly Are Cold Wallets?
A cold wallet is a storage solution that stays offline, which makes it incredibly difficult for hackers to access. In essence, it’s the “vault” of the crypto world. Think of it as locking your valuables in a safe buried underground instead of leaving them in a bag by the door. Cold wallets stand in sharp contrast to hot wallets, which are connected to the internet and are much easier to exploit.
One infamous case that shows the dangers of hot storage was the Mt. Gox hack back in 2014. Over 850,000 Bitcoin vanished, and thousands of investors were left empty-handed. Most stolen funds were in hot wallets – the lesson is clear, isn’t it?
How to Set One Up
You don’t need to be a tech wizard to set up a cold wallet. It’s surprisingly straightforward, and here’s a quick guide you can follow:
- Get a hardware wallet: Trusted brands like Ledger or Trezor are reliable, industry-vetted options. Order directly from the manufacturer to avoid tampered products.
- Set up the device: Follow the manufacturer’s instructions carefully. During setup, you’ll be given a seed phrase – 12 or 24 words crucial for recovery. Write this down, and guard it with your life.
- Transfer your funds: Connect your wallet to a secure computer momentarily, then transfer your crypto. Once done, disconnect and store the wallet somewhere safe.
It’s crucial to test the wallet after setup by sending a small, insignificant amount first. Remember, it’s worth taking an extra hour to ensure everything is functioning properly rather than rushing and risking mistakes.
When to Move Funds Off an Exchange
Knowing the “when” is just as important as knowing the “how.” Keeping your assets on an exchange long-term is like leaving your paycheck in a stranger’s pocket and hoping they don’t walk away with it. Even the largest and most popular exchanges are not immune to hacks – just Google the “Binance hack” of 2019, where users lost 7,000 BTC in a single attack.
So, when should you transfer your funds? A good rule of thumb is to immediately move crypto you don’t intend to trade in the short term. If you’re saving up Bitcoin, Ethereum, or any other tokens for a future goal or investment, cold storage is non-negotiable. Think of it like moving your retirement savings to a high-security vault rather than leaving them sitting exposed.
That said, it’s also a good idea to periodically review your holdings. Are your funds on multiple exchanges? Are you trading actively, or are most of your coins just gathering digital dust? Answering these questions will tell you if it’s time to make the move.
“Security is never convenient, but neither is rebuilding your life after a devastating loss.”
Protecting your assets might seem tedious at first, but the peace of mind that comes with it is priceless. Imagine waking up to news of a massive exchange breach and calmly knowing that your funds are untouchable. Isn’t that worth the effort?
By now, you’ve taken a big step in getting to grips with cold storage, which is a major player in safeguarding your crypto investments. But what about the “weak links” – like your online or mobile habits? Can those everyday actions open the door to vulnerabilities? Stick with me, because in the next section, we’ll uncover smart strategies to secure your devices and online sessions.

What Are Crypto Exchanges?
Crypto exchanges are platforms that offer the facility required to trade, buy or sell cryptocurrencies. It is very difficult to bypass these entities, especially if you plan on investing or purchasing cryptocurrencies. As such, it is vital to discuss the security threats associated with them, knowing fully well that they are the major cryptocurrency gateway.
Why Do You Need to Consider Security When Choosing an Exchange?
A majority of crypto exchanges run a centralized venture. As such, there offer intermediate services by acting as the middlemen that facilitate trades between users and they receive fees in the form of commission for their troubles. For this system to work seamlessly, centralized exchanges must custody users’ assets. Hence, exchanges also provide custodial wallets, which store the private keys on behalf of users. And judging by the recurring security crises linked to this crypto exchange system, security remains an integral requirement when choosing a crypto exchange.

Over the years, we have witnessed the devastating effects of using crypto exchanges with porous security systems. Between 2011 and 2014, Mt.Gox, one of the most dominant Bitcoin exchanges at the time, suffered a series of security breaches, which led to the theft of over 800,000 BTC. This remains the biggest crypto heist in history. More recently, Kucoin lost $240 million worth of cryptocurrencies to hackers.
In hindsight, I believe that many of the victims of these incessant attacks would wish to have done things differently, which is why it is crucial to learn from history. In this section, we will explore the security parameters that you should look out for when using a crypto exchange.

Crypto Exchange Security Tips
Cautiously Use Exchange’s Hot Wallet
From details of the successful hacks recorded over the years, it is clear that attackers majorly focus on breaching hot wallets for the obvious reasons. Crypto exchange wallets hold pooled assets of users and there is no way such wallets would go unnoticed. In essence, consider using crypto exchange wallets sparingly to limit your exposure to security threats. For those who cannot do without these services, they should allocate just a small fraction of their crypto holdings to crypto exchange wallets. The bulk of your funds should remain in a cold wallet.
Use A Strong and Unique Password
You ought not to use a password for multiple exchange accounts. Ensure that all your passwords are unique and strong. This precaution eliminates the risks of recording a domino effect. In other words, you do not need to worry that the porosity of one of your crypto exchange accounts will affect the others.
Opt for Two-Factor Authentication
Ascertain that your crypto exchange offers a secondary layer of protection in the form of two-factor authentication. It is advisable to restrict your activities to exchanges that support this model of identity verification processes. Check to see that 2-FA is a primary security layer available for all users. Note that you might have to activate it once you create your account.
Choose Advance Cold Wallet Security
It is common for exchanges to incorporate cold storage systems for users’ assets and a majority of their holdings. This approach makes it a tad difficult for hackers to successfully hack the entirety of the exchange’s asset storage system. As such, the assets that are prone to attacks are those stored in the platform’s hot wallets. More importantly, exchanges should distribute assets across multiple hot and cold wallets to reduce security risks significantly. It is even more impressive if the exchange provides insurance cover for users. With this, users are rest assured that security breaches are inconsequential to the safety of their funds.
Analyze Data Protection Systems
It is not just your asset that is vulnerable when you utilize a crypto exchange. You also have to be cautious of the exchange’s approach to data collection and protection. Depending on the type of crypto trading platform you opt for, you might need to scale KYC procedures and submit personal data ranging from your banking details to identity documents. Just as the exchange is tasked with the responsibility of keeping your funds safe, it must also leave no stone unturned to ensure that submitted data does not fall into the wrong hands. On your part, you should research the platform’s data collection and protection policy and confirm that the exchange is competent enough to handle users’ data.
Check the Reputation of The Exchange
The easiest way to assess the competency of a crypto exchange is to research its historical background. When you do this, you can unearth past security crises recorded by the exchange and how it resolved such issues. This information will help you determine how committed the exchange is to enable a safe environment for users.
Ensure That the Crypto Exchange’s URL Is Correct
Crypto hackers have an array of ways they operate. One of the popular scams you may encounter is a website cloning scheme. Here, fraudsters clone reputable websites and lure unsuspecting victims to give up their account information. Therefore, do not get carried away whenever you want to access your crypto wallet. Make sure that the URL is correct or better still, you can bookmark the website. The same goes for exchange apps. Try as much as possible to download the official app.
Choose Regulated Exchanges
Without any doubt, the influx of crypto exchange regulations has tempered the crypto security crisis significantly. Exchange managements are committing more resources and manpower to security initiatives. Platforms are collaborating effectively to stop crypto hackers from carting away with stolen funds and the emergence of AML and KYC rules is giving malicious entities something to think about. Therefore, you should ascertain that your exchange is domiciled in a region or country with strict crypto regulations. To an extent, this might spur the exchange to provide standard security infrastructures.
Use A Decentralized Exchange
For individuals that are not comfortable with sharing their private data or subjecting their keys to third-parties, you can opt for decentralized exchanges, like Uniswap, which do not require KYC or custodial-based trades. With a decentralized exchange or DEX, you can evade some of the security risks peculiar with centralized exchanges. You do not need to store your assets on hot wallets, nor will you worry about losing your private data to malicious entities.

DeFi Security
Speaking of decentralized solutions, they have their fair share of disadvantages. For instance, the crypto market recorded more hacks in the decentralized finance sector last year. The growing demand for open finance has drawn the attention of hackers to the DeFi market. This, coupled with the nascent nature of the sector, has exposed users to more risks, most especially rug pull scams.
What Is A Rug Pull Scam?
Rug pulls are coordinated scams that capitalize on the unregulated nature of DeFi to create fraudulent investment opportunities and attract unsuspecting victims. Going by the current system of the DeFi landscape, anyone can create a project, slap the DeFi tag on it, attract investors, and steal their funds once the funding stage is over. The security threats posed by this scam are more difficult to isolate because DeFi promotes the animosity of developers. Thus, more often not, there is no way of catching these perpetrators, which is DeFi hacks accounted for more than half of the total crypto security incidents recorded in 2020.
As long as DeFi keeps offering some of the most impressive yield generating opportunities, expect the sector to continue to attract illicit entities. Hence, it has become risky to invest in DeFi projects without carrying out the proper research and utilizing the right tools. Knowing fully well that DeFi is an unregulated sector and there is no way of recovering lost funds, it is left for investors to go the extra mile to identify viable DeFi investments.
So, you may be wondering: How do I evade the apparent security threats associated with DeFi? Here is how.
DeFi Security Tips
Opt for Audited DeFi Products
It is not enough to base your research on biased reviews you find online. When it comes to DeFi, it is vital to capitalize on the open-source culture of the sector and analyze the underlying codes. Even if you lack the technical expertise to do this, you should ensure that the project has been audited by reputable auditing firms. To an extent, this will help ascertain that attackers cannot take advantage of bugs to steal users’ funds.
Confirm That the Project Has Reputable Backers
A majority of top crypto brands are looking to invest or integrate with promising DeFi projects, since that it is fast becoming a viable alternative to conventional financial systems. Therefore, if you notice that several established brands are backing a DeFi project, it might indicate that the project is not run by faceless entities and that there is a working product.
Check for Liquidity Locking Implementations
It is imperative to restrict your DeFi investment activities to protocols or projects that agree to implement liquidity locks for the DEX pools. Liquidity locks make it impossible for liquidity providers or project teams to withdraw either liquidity tokens or the tokens allocated to founders before a predefined time. This security measure ensures that investors are not susceptible to rug pulls. It also shows the project team’s commitment to the long-term sustainability of the protocol.
Consider DeFi Insurance
DeFi insurance is an emerging concept that encapsulates the provision of insurance services to DeFi users. With this, investors can rest assured that losses due to unforeseen security loopholes can be claimed. That said, this concept is still in the experimental stage as there are no industry-wide standards introduced yet. However, you should consider exploring the possibilities that DeFi insurance provides in the meantime and check if it is compelling enough for you.
Stick to Established Projects
Perhaps, you will better off sticking to tested and trusted DeFi solutions. These protocols have shown beyond a reasonable doubt that they offer viable and security-conscious products. Therefore, rather than gamble on the unknown, you could limit yourself to established projects.

How to Outsmart Common Scams
Scams aren’t just a minor inconvenience—they’re a multi-billion dollar problem in the crypto space. And trust me, they’re becoming more creative each day. If you’ve been wondering how to recognize and avoid these traps, you’ve come to the right place. As someone who’s spent years understanding this growing threat, let me show you exactly what you need to watch out for.
A famous line comes to mind:
“It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.” – Warren Buffett.
Well, in crypto, it takes five seconds to lose your funds if you’re not paying attention. Let’s not let that happen.
Impersonation on Social Media
Picture this: you’re scrolling through Twitter when a popular crypto influencer posts a giveaway. “Send 0.1 BTC, and I’ll send back 0.2 BTC!” Sounds great, right? Except it’s a scam, and that’s not even the real influencer. Fake accounts pretending to be trusted people or “exchange support” agents are everywhere.
Here’s how you catch them:
- Look for subtle typos in usernames like @crypt0king instead of @cryptoking.
- Check the verification badge. If they don’t have one, red flag.
- Never share your private keys or seed phrases. A legitimate company or person will never ask for them—not in public, not in private, not ever.
For instance, a 2022 report by the Federal Trade Commission revealed scammers tricked users out of more than $100 million through fake crypto giveaways. Don’t be part of that statistic.
Ponzi Schemes and “Too-Good-To-Be-True” Deals
Would you trust someone who promises guaranteed 100% returns in 24 hours? It’s tempting, I get it. But these are classic Ponzi schemes. They rely on “investors” bringing in new money to pay earlier participants—until the house of cards collapses.
A great example of this is OneCoin, which conned victims worldwide out of $4 billion. They marketed themselves as the next Bitcoin, offering irresistible returns—but it turned out to be one of the largest crypto scams ever. Remember, if someone’s offering flashy gains with no risks, it’s exactly the risk you should avoid.
So, what’s the move? Follow these tips:
- Research projects thoroughly. What’s their track record, and who’s behind them?
- Watch out for pressure tactics. If they’re telling you “Invest now or miss out,” walk away.
- Stick to trusted platforms when investing in new projects or opportunities.
Rug Pulls and Fake Tokens
Ah, “rug pulls.” They’re the grim reapers of DeFi and token launches. This is how it works: a project launches a new token, hypes it up with slick marketing, and gets tons of people excited. The price surges as everyone piles in. Then, the developers disappear—along with your money.
Take the Squid Game token, for instance. Launched in 2021, it exploited the massive popularity of the Netflix show. The price skyrocketed over 23 million percent (yes, you read that number right) before it collapsed. Investors lost everything. All because they didn’t spot the warning signs.
Here’s how to stay safe:
- Check liquidity locks. If a token’s liquidity isn’t locked, the creators can pull the funds out at any time.
- Read the smart contract code. If you’re not a techy, find someone who is. Certain red flags, like functions allowing total withdrawal, are dealbreakers.
- Research the team. Are they public and credible, or just faceless profiles?
It’s all about verifying before trusting, and honestly, it doesn’t take long to spot inconsistencies if you actively look for them.
The reality is harsh—these scams prey on everyone from absolute beginners to seasoned traders. What’s important is knowing that you have the tools to fight back. And here’s the thing: once you start recognizing these red flags, you’ll feel in control. You’ll feel empowered.
But speaking of tools, what are the best ones out there for crypto security? You’re about to find out. Keep reading, because I’ve gathered some resources that can transform your approach to safety.

Tackling Mobile and Online Vulnerabilities
We live in a world where most things are accessible through the screens of our phones or computers. Cryptocurrencies are no exception. Whether you’re checking your portfolio, making transactions, or interacting with DeFi platforms, these devices play a huge role in managing your investments. But here’s the real question: are they secure enough?
A single vulnerability on your phone or in your browser could expose your crypto to very real risks. The stakes couldn’t be higher, yet it’s surprising how often people overlook this. Let’s fix that today. By understanding these vulnerabilities and acting on them, you’ll reduce the risks while staying one step ahead.
Security Basics for Mobile Users
Your smartphone is like a gateway to your digital world, and keeping it secure is non-negotiable. The first thing to do? Treat crypto-related apps differently than you treat your Candy Crush addiction. Here’s how:
- Install apps only from official and verified app stores. Phony wallet apps designed to steal your keys have slipped onto app platforms in the past, tricking unknowing users.
- Enable biometric locks for your crypto apps. This adds an additional layer of security, so even if your phone gets into the wrong hands, your crypto apps won’t be easy to access.
- Keep your mobile OS updated. Hackers are always improving, but fortunately, so are developers. Updates often patch vulnerabilities that could otherwise be exploited.
- Use a separate mobile device for crypto. If you’re serious about security, consider using a dedicated phone solely for crypto purposes, free from distractions and risks like random app downloads.
Think about this: would you walk around with your life savings in your pocket every day? That’s essentially what happens if your phone isn’t protected. “Digital possessions hold enormous value – treat them like gold.”
Secure Your Browser Sessions
Your computer’s browser can make or break your crypto’s safety. If you interact with wallets, exchanges, or DeFi platforms via a web browser, you’re exposed to risks like phishing scripts and malicious ads. Let me share what has worked for me:
- Opt for privacy-focused browsers like Brave. These browsers block ads, trackers, and scripts that could compromise your sensitive data.
- Use browser extensions cautiously. Hackers love to disguise malware as useful tools. Before installing an extension, ask yourself if it’s genuinely necessary—and always verify its legitimacy.
- Activate anti-phishing tools. Some browsers and extensions recognize phishing attempts and can stop you from visiting harmful websites. Use them.
- Avoid storing passwords in your browser. A dedicated password manager, especially one that encrypts data, is a much better option. You’ve worked too hard for your crypto – don’t give away the keys to your vault this easily.
Here’s a disturbing example: In 2021, a meta-mask browser plugin exploit was uncovered, enabling attackers to drain funds from wallets. If victims had taken a moment to verify the authenticity of the extension, losses could’ve been avoided. Always stop, think, and verify before making a move.
Beware of Public Wi-Fi
Using public Wi-Fi might seem harmless, but it could easily be one of the biggest mistakes you make when handling crypto online. Did you ever stop to think about who else is using that same free coffee shop Wi-Fi? Hackers often camp out on these networks, waiting for someone to log into an exchange or wallet without protection.
Here are the dangers and fixes:
- Public Wi-Fi is a hacker’s playground. The “man-in-the-middle” attack is a common trick on unsecured networks where an attacker intercepts and steals your credentials or transaction details.
- Use a VPN every single time. A Virtual Private Network encrypts your connection, making it impossible for prying eyes to see what you’re up to. Even if someone detects your activity, they won’t be able to decode it.
- Turn off automatic Wi-Fi connections. This stops your device from unknowingly connecting to fake Wi-Fi networks set up by attackers to mimic real ones (e.g., “Starbucks Free Wi-Fi” could easily be a trap).
- Never perform sensitive tasks on public Wi-Fi. If you must check crypto portfolios or make transactions, switch to your mobile data. It’s worth the tiny cost compared to the potential risks.
An unsettling report from Symantec once revealed that hackers created duplicate Wi-Fi networks designed to mirror popular public hotspots. The unsuspecting victims? Individuals casually logging into their accounts, unaware that every keystroke was being recorded. Don’t be that person.
Now that you’ve gotten your devices secure, don’t think the threats stop there. Scams—yes, those cleverly crafted traps that seem too good to be true—are a growing menace to crypto investors. Ready to outsmart them? Let’s look at how, up ahead.
Stay in Control of Your Crypto Security
At this point, you’ve seen the risks, the tools, and the strategies you need to secure your crypto investments. But the real question is: how will you make security a part of your daily routine? Because let’s face it, every tip you’ve read here is only as good as the effort you put in. Let’s tie it all together so you can build a convenient and foolproof system for protecting your assets.
Make Security a Habit
Security isn’t about doing one or two big things and calling it a day – it’s about consistently adopting small, smart actions. It’s like locking your front door: you don’t think twice about it, you just do it because it’s second nature. Your crypto security should feel the same way.
- Double-check everything: Whether it’s transaction details, wallet addresses, or the websites you visit – mistakes happen fast, but they last forever in crypto.
- Rotate passwords regularly: I know, it’s annoying. But if your passwords are easy to guess or re-used across platforms, you’re begging to get hacked.
- Stick to trusted resources: Scammers won’t hesitate to set up fake support pages or wallets. If you’re unsure about something, revisit platforms you trust instead of acting on impulse.
The idea here is to build habits that take little effort once you’ve implemented them but yield huge security benefits over the long haul.
Invest Time in Learning Today, Stay Safe Tomorrow
Here’s the thing about crypto: it’s fast-paced and constantly changing. Hacks get smarter, scams evolve, and regulations shift. Keeping up may sound exhausting, but like anything, it’s manageable when approached the right way.
Think of it this way: spending a couple of hours now to learn about your wallet options or testing out a 2FA app can save you thousands in losses down the line. Take your time exploring hardware wallets. Even browsing forums or joining communities can help you catch advice or warnings from people who’ve already faced challenges and learned the hard way.
One interesting study by Chainalysis showed that users actively engaging in crypto communities are far less likely to fall victim to scams compared to those who go it alone. There’s no shame in asking questions – I’ve learned tons just by interacting with fellow crypto enthusiasts.
Conclusion: Protecting Your Assets is Protecting Your Future
Let’s keep it real – securing your crypto isn’t about paranoia, it’s about financial self-respect. You’ve worked hard to earn what you own, and with just a bit of consistent effort, you can ensure it stays in your hands. That’s the point of everything we’ve talked about here.
By incorporating these tips into your life, you’re not just reducing risks – you’re setting yourself up for worry-free investing. Whether you’re a day trader, long-term hodler, or just someone exploring crypto’s possibilities, security is non-negotiable. Make it a priority. You’ll thank yourself later when the sleepless nights and near-misses are avoided entirely.
Always stay curious and cautious out there. The crypto world is evolving, and so should your defenses. Check out trusted resources when you’re in doubt, and remember – the most valuable asset in your wallet is your ability to stay proactive. You’ve got this.
